Discover the importance of vendor due diligence in ensuring compliance and protecting your business from third-party vulnerabilities.
During the pandemic, numerous companies found that they couldn’t get essential components for their products. This caused many to lose sales, temporarily close, and in some cases even go out of business. That time period has since receded, but organizations still significantly depend on vendors of all kinds. And those relationships can expose businesses and agencies to disruptive risks—not only supply shortages, but also data breaches and reputational damage.
It’s crucial to know your customer (KYC) and it’s just as crucial to know your vendor (KYV). Whether in the private or the public sector, risk and fraud professionals need to be current on the processes and the best practices of vendor due diligence (VDD) to manage risks associated with potential or current third-party suppliers.
Jump to ↓
Importance of vendor due diligence
Best practices of vendor due diligence

White paper
Adverse media screening: Harness the power of artificial intelligence to mitigate risks
Access full whitepaper ↗
What is vendor due diligence?
Vendor due diligence (VDD) is a comprehensive process for evaluating third-party vendors before establishing or maintaining business relationships. This allows the organization to make an informed decision about onboarding a vendor or continuing with an existing one. The objective, of course, is to shield the business or agency from perilous partnerships and possible disaster. Thorough vendor due diligence also protects customers or clients from risks such as data exposure caused by cyber-attacks on third parties.
The vendor due diligence process is similar to those followed in other due diligence processes:
1. Initial assessment
The organization starts by conducting a risk assessment. Preliminary screening typically includes background checks to identify any relatively obvious red flags. During this evaluation phase, many organizations send questionnaires to potential suppliers requesting information on internal processes and risk management protocols.
2. Information gathering
Then it’s time to dig deeper. The organization pulls together all available documentation to verify a potential vendor’s identity, including the supplier company’s beneficial ownership and management structure. This step also involves researching any past or ongoing legal disputes, bankruptcy filings, sanctions, and adverse media coverage.
3. Risk evaluation
Once this information is gathered, the organization implements a risk analysis. Experts (either internal or external) in areas including cybersecurity, supply chain, finance, and operations should review this information to assess potential risks.
For instance, a financial analyst could pore through the potential vendor’s financial statements, accounting practices, cash flow, and internal controls, alert to any anomalies that might suggest problems down the road. A legal expert might dig into the vendor’s contracts, intellectual property, and litigation history, as well as its compliance with relevant regulations and industry standards, such as anti-money-laundering (AML) rules and environmental, social, and governance (ESG) requirements.
Risk evaluation also requires an organization to clarify its vendor risk tolerance. A useful technique is risk scoring. In evaluating risk levels, the organization will need to determine criticality. A vendor would be considered critical if the unavailability of its product or service significantly disrupted the organization’s operations. It would also be high-risk if its product or service couldn’t be quickly fulfilled by another vendor. Additionally, the supplier would be categorized as high-risk if, for instance, it was given access to the organization’s data. The higher the risk, the more rigorous the VDD.
4. Decision and implementation
Here the organization documents the decision to approve or reject the vendor relationship. If it chooses to approve, it can include contract language limiting exposure to third-party risks.
5. Ongoing monitoring
Even after onboarding the vendor, the organization should conduct regular monitoring and assessment to detect any significant changes, new risks, or operational irregularities. These issues might require the organization to terminate the partnership.
Importance of vendor due diligence
In today’s interconnected business environment, where organizations increasingly rely on outside parties for critical functions, VDD’s importance can’t be overstated. Effective know-your-customer vigilance reveals potential vulnerabilities within a supply chain, helps maintain regulatory compliance, and protects organizations against financial and operational disruptions.
Examples of damage due to vendor-related risks are depressingly numerous. To spotlight two major instances:
- Target’s massive 2013 data breach, which occurred when hackers stole network access credentials from one of the retailer’s HVAC vendors.
- In 2020, cyber-criminals inserted malware into IT vendor SolarWinds’ network management software, which opened a window to tens of thousands of business and government networks.
Without proper VDD, organizations can face significant costly consequences, and third-party data breaches are just one of them. Businesses and agencies can be hit with financial penalties if a vendor isn’t in compliance with government regulations. Providers experiencing operational problems can snarl supply chains, wreaking havoc with organizations’ stability. All this underscores the fact that robust vendor assessment is more than a compliance exercise. It’s a business imperative.
Best practices of vendor due diligence
To address this imperative effectively, organizations should familiarize themselves with current VDD best practices:
- Risk-based approach: A risk-based approach focuses resources on vendors posing the greatest potential risk, with assessment depth depending upon the vendor relationship’s criticality and potential risk impact.
- Standardization and automation: Consistent frameworks and metrics help organizations evaluate and improve their vendor due diligence. Leveraging technology, including AI-powered tools, can automate and streamline the collection, analysis, and management of vendor information.
- Cross-functional collaboration: Input from relevant experts and stakeholders within the organization (IT, legal, procurement, compliance, etc.) provides a more comprehensive risk assessment.
- Documentation and centralization: An organization should maintain thorough records of all VDD decisions and risk mitigation plans so that they’re available to all stakeholders.
- Continuous monitoring: This is essential because vendor information, business conditions, and regulations are subject to change. Organizations also should set up more frequent VDD reviews for critical and high-risk third-party vendors.
While leveraging technology is a key best practice, these digital tools must be able to conduct vendor due diligence thoroughly and efficiently. Thomson Reuters Risk & Fraud Solutions can help organizations implement robust third-party risk management. Powered by CLEAR, an investigation platform that rapidly analyzes a wide variety of large datasets to deliver pertinent know-your-vendor information.
CLEAR provides a trustworthy single technology resource for:
- Validate identities to prevent fraud before onboarding
- Screen entities for global sanctions to identify risks
- Assess risk tolerance levels before entering a business relationship
- Monitor on-going activity and be alerted of new adverse matters
- Investigate concerns that could harm your business
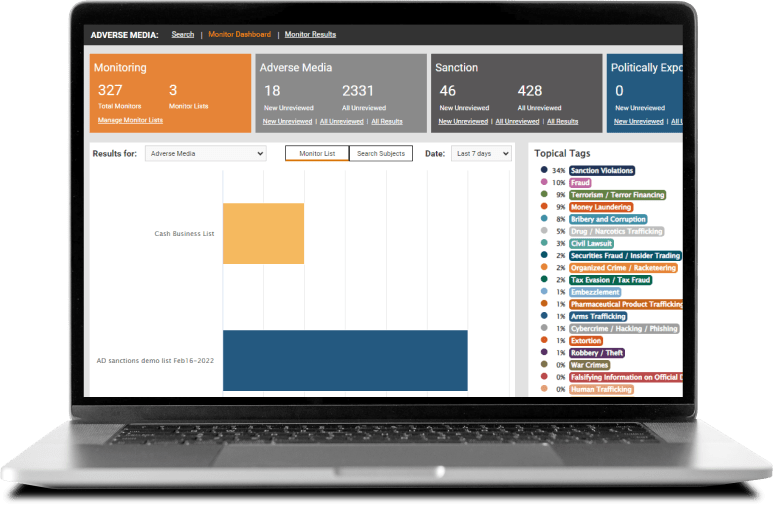
CLEAR Adverse Media
Quickly receive and manage organized adverse-media articles and sanctions lists
Request free demo ↗Thomson Reuters is not a consumer reporting agency and none of its services or the data contained therein constitute a ‘consumer report’ as such term is defined in the Federal Fair Credit Reporting Act (FCRA), 15 U.S.C. sec. 1681 et seq. The data provided to you may not be used as a factor in consumer debt collection decisioning, establishing a consumer’s eligibility for credit, insurance, employment, government benefits, or housing, or for any other purpose authorized under the FCRA. By accessing one of our services, you agree not to use the service or data for any purpose authorized under the FCRA or in relation to taking an adverse action relating to a consumer application.