CLEAR Risk Inform
Quickly receive summarized insights to prevent fraud and detect risk
Help protect your organization against potential hazards with CLEAR Risk Inform, a customizable risk assessment tool that delivers adverse indicators on subjects of interest
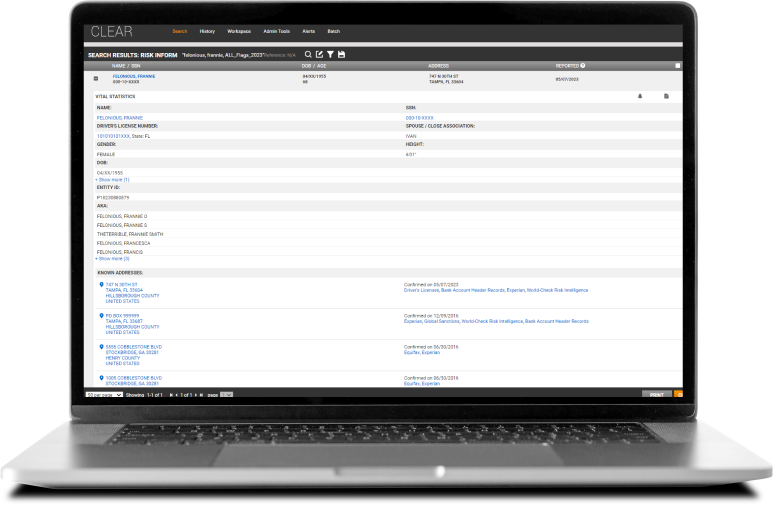
Enhance your risk management workflow with a fully configurable solution
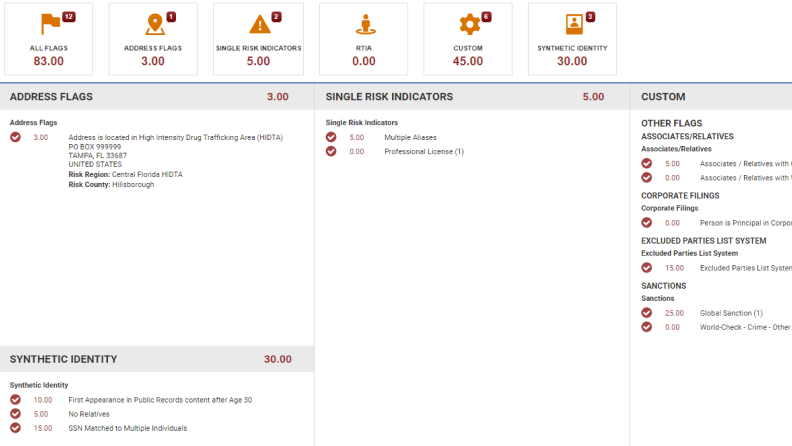
Quickly obtain adverse flags during risk assessment
Save time during analysis by receiving flags for synthetic identities, criminal and arrest records, sanctions, and other risky affairs.
Explore more features
Have questions?
Contact a representative
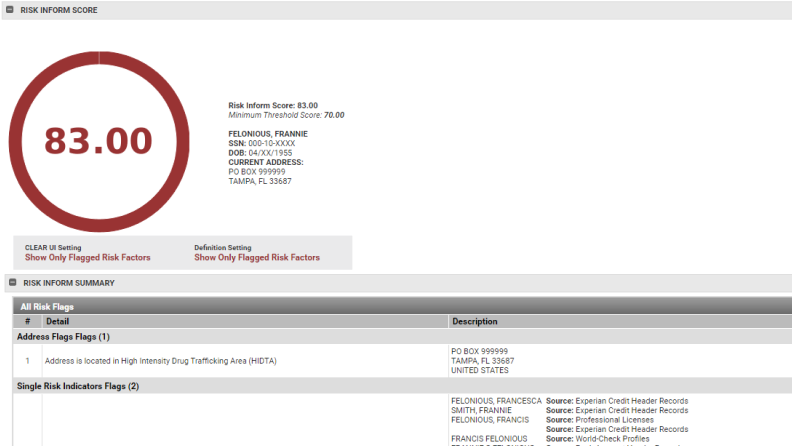
Review your most adverse subjects first with calculated risk scoring
Prioritize high-risk subjects for further investigation based on calculated risk scoring set by your organization.
Explore more features
Have questions?
Contact a representative
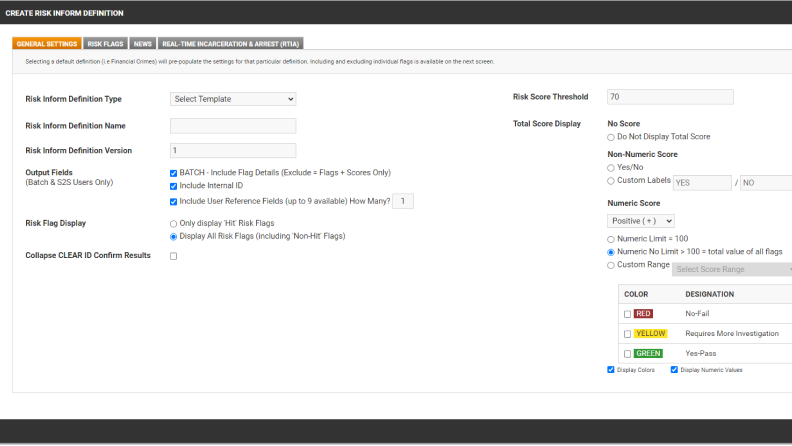
Meet your risk management needs with customizable criteria
Increase productivity among users with fully customizable risk settings that fit your organization’s specific needs.
Explore more features
Have questions?
Contact a representative
Corporate and government professionals use CLEAR Risk Inform to mitigate risk and prevent fraud
Financial institutions
Quickly assess risk during onboarding to prevent fraud and follow Bank Secrecy Act (BSA) regulations.
Healthcare
Get immediate insights for providers and beneficiaries through a calculated risk score, configurable definitions, and separation of high- and low-risk subjects.
Insurance
Easily conduct risk assessments during customer onboarding and help your special investigation unit (SIU) department investigate potential fraudulent claims.
Unemployment
Obtain an automated risk assessment and calculated risk score for individuals and businesses filing unemployment insurance claims.
Vendor due diligence
Ensure you conduct business with low-risk companies by using configurable definitions and calculated risk scoring based on your organization’s risk appetite.
Retail
Understand potential risks when doing business with customers and before shipping products online.
The value of CLEAR Risk Inform
40% more efficient risk assessment
Experienced by customers from a variety of industries such as banking, insurance and securities, and cryptocurrency.
30% faster with processes to meet compliance requirements
Realized by customers with annual revenue ranging from $15 million to $10 billion.
7- to 12-month ROI
Ninety-four percent of surveyed organizations saw a return on their investment within seven to 12 months.
“My favorite thing about CLEAR Risk Inform is the ease of use. Two inputs — name and state — generally put you on a path to all the due diligence you need at least as a first screen.”
Neal Shipley
CEO, Capital Foundry LLC
Questions about CLEAR Risk Inform? We're here to support you.
888-728-7677
Call us or submit your email and a sales representative will contact you within one business day.
Contact us
CLEAR Risk Inform support
Already a customer?
Thomson Reuters is not a consumer reporting agency and none of its services or the data contained therein constitute a “consumer report” as such term is defined in the Federal Fair Credit Reporting Act (FCRA), 15 U.S.C. sec. 1681 et seq. The data provided to you may not be used as a factor in consumer debt collection decisioning; establishing a consumer’s eligibility for credit, insurance, employment, government benefits, or housing; or for any other purpose authorized under the FCRA. By accessing one of our services, you agree not to use the service or data for any purpose authorized under the FCRA or in relation to taking an adverse action relating to a consumer application.